The Dark Web has only been recently identified, but its cloak of invisibility has prevented investigators from finding out too much about it. It is that part of the internet that is not indexed by mainstream search engines. It is widely known as a Criminal’s Den, and the latest research is proving that it indeed is. In a study by two researchers (Thomas Rid and Danial Moore of Kings College, London), 3000 live Dark Websites were studied for nearly two months in 2015. It was found that 57% of the websites involved illegal activities and illicit materials. Recent studies (in 2019) by Doctor Michael McGuires, University of Surrey, have shown that the conditions inside the Dark Web have worsened.
Since 2016, websites on the Dark Web that could harm other enterprises have increased by over 20%. Almost anything illegal goes on the Dark Web. From stolen subscription credentials, counterfeit money, and credit card numbers to all types of illicit and counterfeit drugs and banned firearms have now flooded the Dark Web. Usernames and passwords have been bought and hackers can be hired to attack computer networks, on behalf of criminal organizations. But there is a legitimate side too. And this includes various privacy-seeking websites and networks including some of the top local apps. These niche casual dating platforms use their presence on the dark web for privacy and discretion naturally filtering out their user base rather than for any clandestine reasons. There is a lot more to the dark web than simply its stigma. The brief review that follows tries to answer the question — What is The Dark Web?
The Deep Web
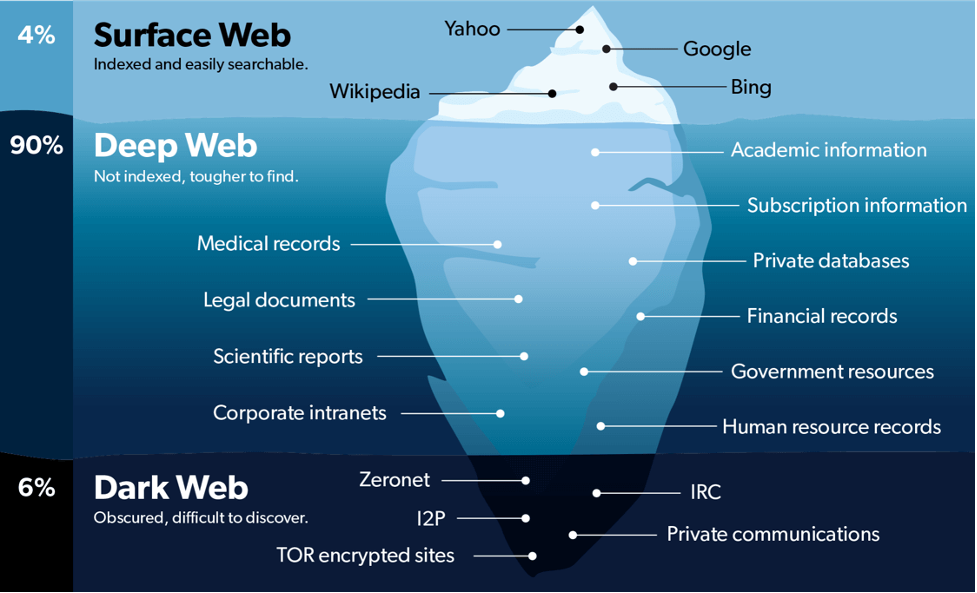
The ‘Dark Web’ is a subset of the ‘Deep Web’. The Deep Web includes anything that is non-indexed on the Internet. It is therefore inaccessible via a listed search engine like Google. Deep Web content is only partially from Dark Web. Deep Web also includes any content that its owners have blocked Web Intruders, Hackers, and Callers from indexing.
The Deep web content also includes content that requires ‘Sign-In’ credentials or is behind a Paywall. For example, membership websites, confidential corporate web pages, and medical records belong to these categories also part of the Deep Web. Recent estimates have put the Deep Web to be about 96% to 99% of the Internet. The remainder, also known as the ‘Clear Web’, is just a tiny portion of the Internet that is indexed officially and is therefore available through a standard search engine or web browser. Only a small portion of the Deep Web comprises the Dark Web.
Enterprise Risk Tools
There are at least 12 categories of Tools or services that present a serious risk to legal enterprises. This risk is in the form of a Data Compromise or a Network Breach. Some of them are:
- Phishing
- Customer Data
- Operational Data
- Financial Data
- Infective Attacks, such as Malware, DDoS (Distributed Denial of Service), and Botnets.
- Espionage, including Service targeting and customization.
- Credentials
- Refunds
- Intellectual Property or Trade Secrets
- Access, including Keyloggers, Exploits, and RATs (Remote Access Trojans)
- Tutorials and Support Services
- Other newer threats.
A Voyager called Tor
The Tor browser travels through the Dark Web as an anonymizing browser and routes the web pages requested by the user, through a series of proxy servers. These proxy servers are operated by thousands of volunteers around the planet, whose main task is to render the user’s IP untraceable and unidentifiable. The results are often unreliable and unpredictable. And the process is extremely slow. But when it works, this brilliant track is magical. The Tor provides glimpses of the nightmarish side of human nature and the spread of criminal activity throughout the world that is unforgettable.
Sights on the Dark Web
These sights are initially indistinguishable from any other site, but differences do exist. The obvious difference is in the naming format. Sights on the Clear Web tend to end in ‘.com’, ‘.co’, or ‘.org’. Dark Web sites end in ‘. onion’. This suffix designates an anonymous hidden service, which can only be reached by the tor network. Also in use on the Dark Websites is the creation of URLs that are almost impossible to remember. This is done by using a scrambled naming structure, and creating unintelligible addresses, such as, ‘xejylvm3z92bca37.onion’.
Conclusion
World-class enterprise security is the goal for all organizations and Encora’s experts practice advanced enterprise security and practices to secure infrastructure, data, applications, cloud, and IoT solutions by detecting and preventing current and future risks.