
For provisioning and configuration management, there are different Infrastructure-as-Code (IaC) tools nowadays. Some of the most famous ones are Terraform, AWS CloudFormation, Pulumi, Ansible, Chef, and Puppet. This article aims to discuss some differences between these tools considering some of their characteristics. In most cases, all tools support or have more than one behavior, but the examples will focus on the default one or what stands out for each tool.
Infrastructure as Code (IaC)
Infrastructure as Code (IaC) automates the process of infrastructure creation and configuration, such as virtual machines, load balancers, networks, etc. An IaC model generates the same result every time it runs [1], avoiding misconfiguration, and saving a lot of time [2].
Categories
First off, let’s divide the IaC tools cited into two categories [6][7]:
1. Provisioning – tools in this category provision infrastructure components for one or more cloud providers. Examples: Terraform, AWS CloudFormation, and Pulumi
2. Configuration Management – tools in this category are responsible for installing and managing software on already existing infrastructure. Examples: Ansible, Chef, and Puppet
Project Phase
Considering a project has two main phases: initial setup and maintenance [3], all tools can be used in both. Combining the categories discussed above (provisioning and configuration management) with these two project phases (initial setup and maintenance), a table can be derived [3], containing the description and the most used tool in each cell as shown in Figure 1.
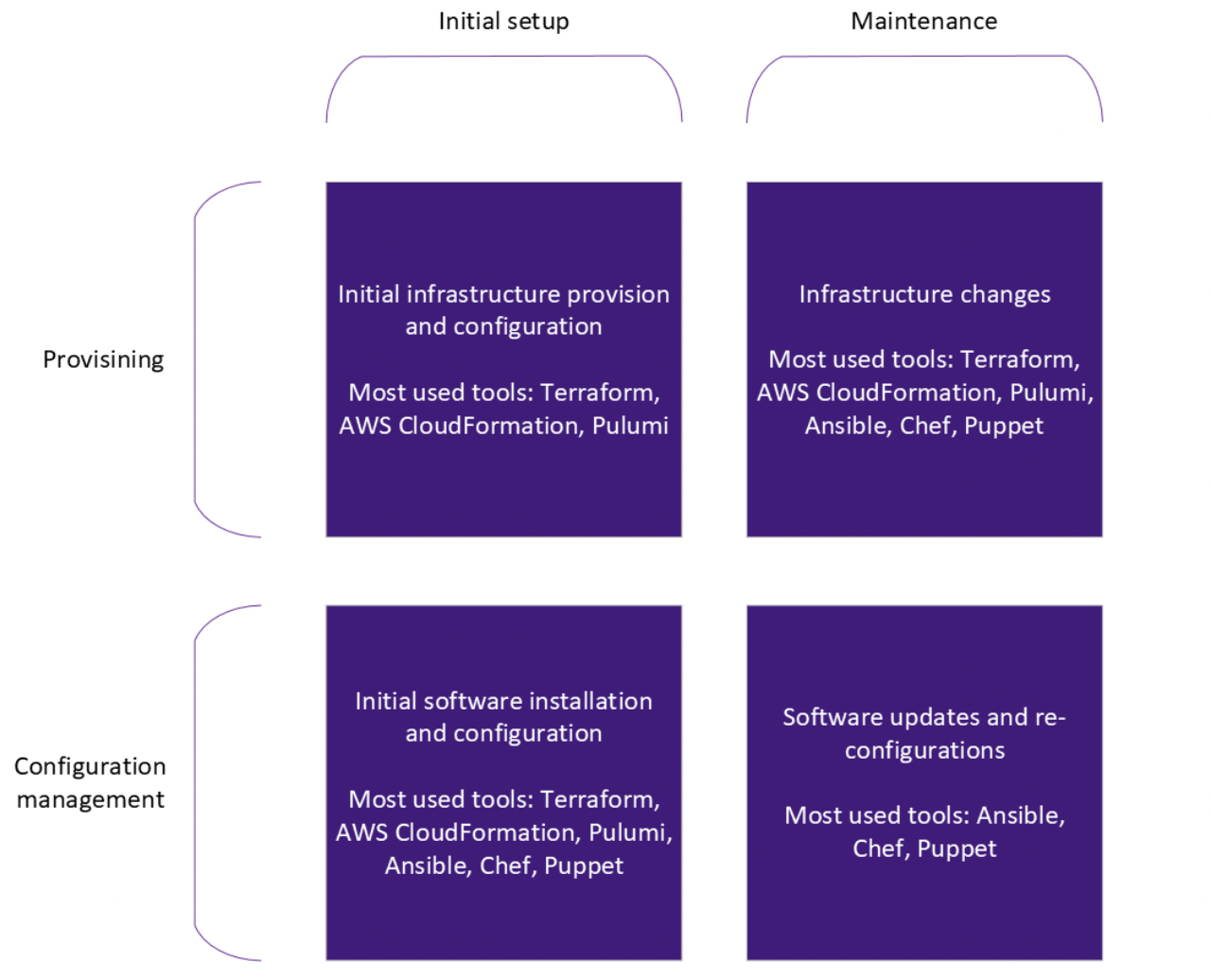 Figure 1 – Table Category vs. Project Phase
Figure 1 – Table Category vs. Project Phase
Declarative vs Imperative Approach
In the declarative (functional) approach, the tool used will perform all required actions to achieve the desired state, which has been configured by you. In the imperative approach (procedural), you need to specify the steps to reach the desired state, and the tool used will only execute the steps.
Examples of tools adopting a declarative approach are Terraform and AWS CloudFormation, whereas examples of tools adopting an imperative approach are Ansible, Chef, Puppet, and Pulumi.
Mutable vs Immutable
Mutable infrastructures allow updates after the software has been deployed, whereas immutable infrastructures do not [4]. The former is more flexible, but it can be more difficult to keep consistency. The latter is more consistent and reliable, but it's more rigid and difficult to change because when any change is needed the infrastructure needs to be recreated [4].
Most of the tools support both approaches. Ansible, Chef, and Puppet are examples of tools that use mainly the mutable approach. For mainly immutable, Terraform, AWS CloudFormation, and Pulumi can be cited.
Agent vs Agentless
Some tools like Chef and Puppet require the installation of additional agents on all servers that need to be configured [8]. Changes are synchronized with these agents, which are responsible for applying the required changes. Other tools like AWS CloudFormation use agents behind the scenes, but they are managed by AWS or by the related cloud provider.
On the other hand, tools like Terraform, Ansible, and Pulumi don’t require the installation of any agent.
Push vs Pull
For the push method, the controlling server will push configurations and artifacts to the destination system [5], usually using SSH. For the pull method, the destination system will pull its configuration and artifacts from the controlling server [5], using an agent installed on the destination system to do that.
Examples of IaC tools that use the push method by default are Terraform, AWS CloudFormation, Ansible, and Pulumi. For the pull method, Chef and Puppet can be cited.
Configuration Language/Configuration File Format
The last difference between the tools this article explores is the configuration language/configuration file format each one adopts. Some of them use well-known formats like JSON and YAML, whereas others use a Domain Specific Language (DSL):- Terraform: HashiCorp Configuration Language (HCL2)
- AWS CloudFormation: JSON, YAML
- Pulumi: TypeScript, Go, Python, C#, Java, or YAML
- Ansible: YAML
- Chef: Ruby DSL
- Puppet: Puppet DSL
Putting It All Together
For a clear view of all characteristics, Table 1 shows a summary of all aspects discussed here.
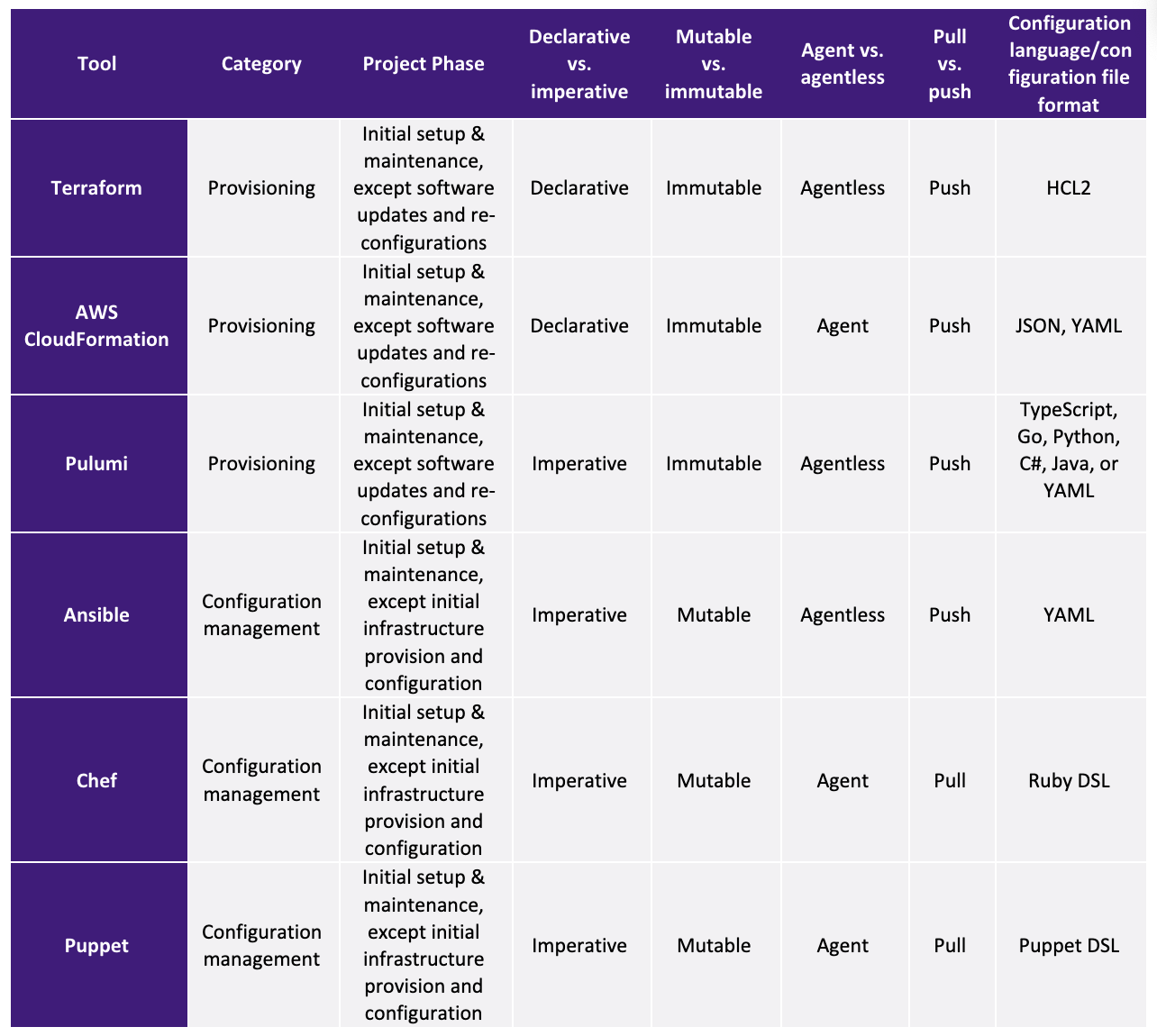 Table 1 - Summary
Table 1 - Summary
Key Takeaways
- When trying to address provisioning and configuration management challenges with IaC there will be plenty of tools available to evaluate
- The definitions and classifications presented in this article provide an easy way to better understand some of the key differences between some of the most common IaC tools in use for provisioning and configuration management
References
[1] Jacobs, M. et al. What is Infrastructure as Code (IaC)? 2022. https://learn.microsoft.com/en-us/devops/deliver/what-is-infrastructure-as-code
[2] Silva, J; Souza, I. Architectural Design Patterns: Infrastructure as Code. 2022. https://www.encora.com/insights/architectural-design-patterns-infrastructure-as-code
[3] TechWork with Nana. What is Infrastructure as Code? Difference of Infrastructure as Code Tools. 2021. https://www.youtube.com/watch?v=POPP2WTJ8es
[4] InMotion Hosting. Ansible vs Terraform. 2021. https://www.inmotionhosting.com/support/edu/ansible/ansible-vs-terraform/
[5] Wikipedia. Infrastructure as Code. https://en.wikipedia.org/wiki/Infrastructure_as_code
[6] Reeves, K. What Is Infrastructure as Code? Overview. 2022. https://blog.cloudticity.com/what-is-infrastructure-as-code-everything-you-need-to-know
[7] Mannambeth, M. Terraform for the Absolute Beginners with Labs. 2023. https://www.udemy.com/course/terraform-for-the-absolute-beginners/
[8] Yevgeniy, B. Why We Use Terraform and Not Chef, Puppet, Ansible, Pulumi, or CloudFormation? 2016. https://blog.gruntwork.io/why-we-use-terraform-and-not-chef-puppet-ansible-saltstack-or-cloudformation-7989dad2865c#64a6
Acknowledgment
This piece was written by João Longo – Systems Architect and Innovation Leader at Encora’s Engineering Technology Practices group, and Marcelo da Silva Pires – Senior DevOps Engineer. Thanks to João Caleffi, Marcelo Mergulhão, Ildefonso de Barros, and André Scandaroli for their reviews and insights.
About Encora
Fast-growing tech companies partner with Encora to outsource product development and drive growth. Contact us to learn more about our software engineering capabilities.